PS4 EXPLOIT FIRMWARE 5.XX REVEALED
Hacker Volodymyr Pikhur has presented and exploit of the PS4’s Rest mode a couple days ago at the Recon Brussels hacking conference. Earlier today, he released the slides and a demo video of his work in action. The slides state he’s been sitting on the exploit for 2 years, and decided to disclose it since Sony does not have a bug bounty.
In the Video below, we can see the hacker running an FTP server, among other things, on the PS4 that was hacked in Rest mode.
According to the developer:
The custom Southbridge silicon, responsive for background downloads while main SoC is off, didn’t help to secure Playstation 4. We explain how a chain of exploits combined with hardware attacks will allow code to run in the context of the secure bootloader, extract private keys, and sign a custom kernel.
I unfortunately did not see the presentation itself, and it is unclear to me how much is being revealed in the slides, although it seems like it could be… a lot.
First of all, it appears the hacker is leveraging (and revealing) a not publicly known kernel exploit on the PS4, leveraging a vulnerability in sys_kldload. There is probably enough in the presentation for people to take this information some step further.
Additionally, the hacker did not stop at kernel access, but proceeded to do some hardware glitching in order to be able to extract the console’s kernel bootloader.
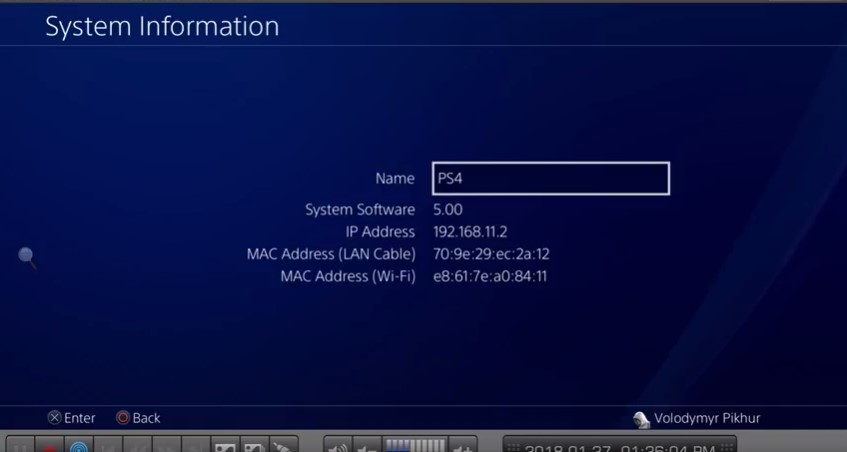
It is unclear whether the vulnerabilities he is describing have been patched in the latest Sony firmware, but his video showcases the kernel exploit running on firmware 5.00.
Update – I received some clarifications from @vpikhur, in particular:
- According to the hacker, the sys_kldload exploit still exists in firmware 5.00, potentially more recent firmwares as well.
- The important point of the video above is that the hack persists after boot, demonstrating what is probably the very first custom firmware on the PS4
- Sony changed their keys in 5.05, but apparently not the signing process.
- The kernel bootloader contains the keys for Rest Mode kernel, which is why it was interesting to get access to it.
Source: @vpikhur